🔐 Understanding AAA, TACACS+, and RADIUS: The Backbone of Secure Network Access
AAA isn’t just about logging in — it’s about knowing who’s on your network, what they’re doing, and proving it later. This post breaks down AAA, TACACS+, and RADIUS in plain terms, with real-world use cases and configuration examples you can actually use.
TACACS+ is not globally deprecated, but its use is declining in favor of RADIUS—especially in environments adopting Cisco ISE, TrustSec, or newer platforms like IOS XR and NX-OS. While still widely used in many enterprise and service provider networks, TACACS+ may not be supported in future Cisco ecosystems.
🔍 Why Access Control Matters
In a world full of logins, passwords, and remote access, network security starts with knowing who’s logging in, what they’re doing, and how long they’re doing it.
That’s where AAA comes in — and it’s more than just a buzzword. This framework is the spine of modern access control in any serious IT environment.
🧱 1. What Is AAA?
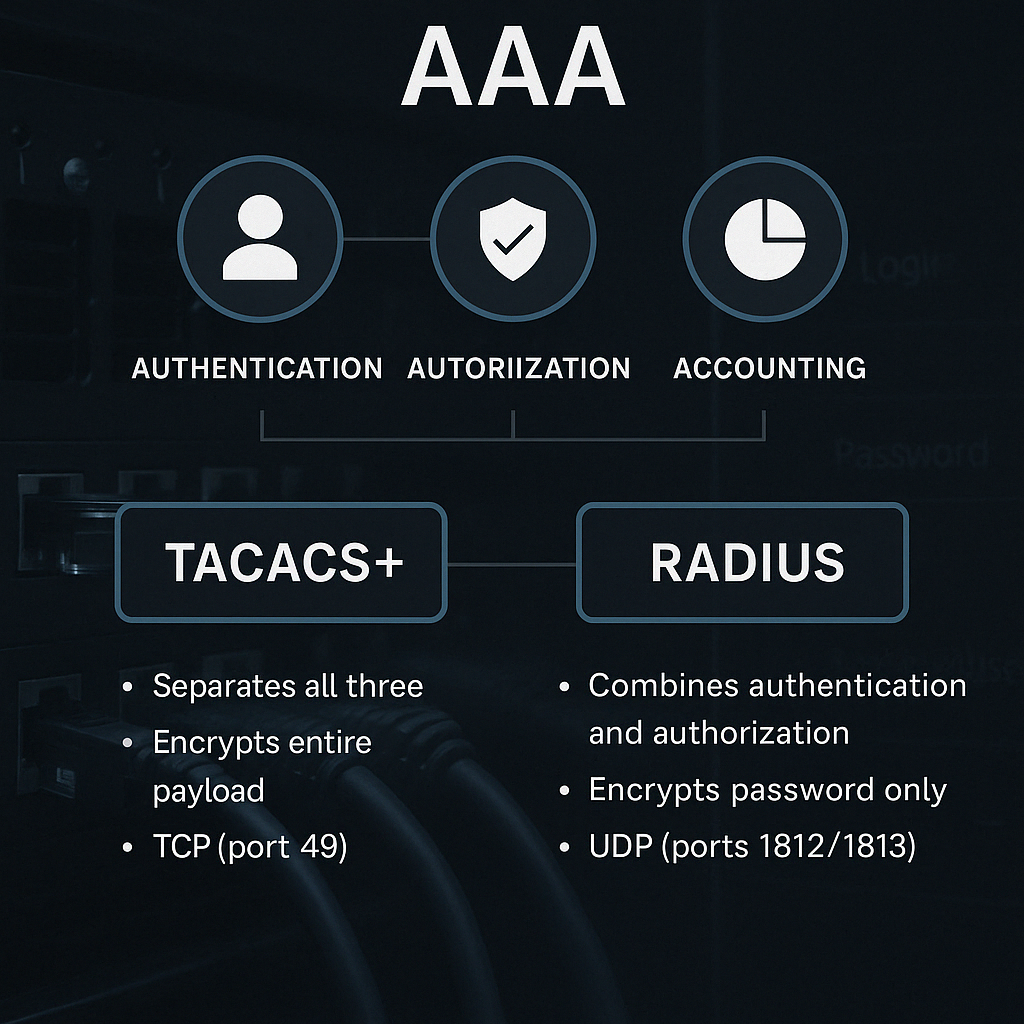
AAA stands for:
- Authentication – Who are you?
- Authorization – What are you allowed to do?
- Accounting – What did you do?
It’s not a protocol by itself, but rather a methodology. And it can be implemented locally or using external servers — enter TACACS+ and RADIUS.
📦 2. TACACS+: Cisco's Full-Stack Access Control
TACACS+ is a Cisco-developed protocol designed to manage device-level access — think SSH or console access to routers, switches, and firewalls.
🔐 Key Highlights:
- Uses TCP (port 49) – more reliable than UDP.
- Encrypts the entire payload, not just the password.
- Allows separate control over authentication, authorization, and accounting.
- Ideal for network device administration in Cisco-heavy environments.
🛠️ Use Case:
💻 Scenario: You're managing multiple Cisco routers and want to control who can run certain commands.
- An engineer connects via SSH to
R1. - TACACS+ authenticates them, then checks if they're authorized to use
conf t. - The server says no, so the engineer gets a permission denied.
- Every action is logged centrally for accountability.
✅ Great for command-level control in enterprise environments.
🧰 Config Example: Cisco IOS TACACS+
aaa new-model
tacacs-server host 10.0.0.10 key MySecretKey
aaa authentication login default group tacacs+ local
aaa authorization exec default group tacacs+ local
aaa authorization commands 15 default group tacacs+ local
aaa accounting exec default start-stop group tacacs+
aaa accounting commands 15 default start-stop group tacacs+
username fallbackadmin privilege 15 secret StrongLocalPass
🔍 Breakdown:
•aaa new-model: Enables AAA framework.
•group tacacs+ local: Try TACACS+, fallback to local login.
•authorization commands: TACACS+ decides what commands are allowed.
•accounting: Logs sessions and CLI commands.
🌐 3. RADIUS: The Standard for Network Access
RADIUS is the industry standard for network login — Wi-Fi, VPN, and even enterprise 802.1X authentication.
🌟 Key Features:
- Uses UDP (ports 1812/1813) – faster but connectionless.
- Encrypts only the password (less secure than TACACS+).
- Combines authentication and authorization in a single process.
- Open standard – works with non-Cisco environments (Microsoft, Linux, etc.)
🛠️ Use Case:
🌐 Scenario: An employee connects their laptop to your corporate Wi-Fi using 802.1X.
- The wireless controller sends login credentials to a RADIUS server.
- RADIUS checks with LDAP or Active Directory.
- Once authenticated, the employee is placed in the correct VLAN based on group membership.
- Login time and data usage are logged.
✅ Ideal for remote user access, VPN, or enterprise Wi-Fi.
🧰 Config Example: Cisco IOS RADIUS
aaa new-model
radius-server host 10.0.0.20 auth-port 1812 acct-port 1813 key RADIUSsecret
aaa authentication login default group radius local
🔍 Breakdown:
• Defines RADIUS server with auth/accounting ports
• Uses RADIUS first, then local fallback
• Often paired with identity services (like FreeRADIUS or Windows NPS)
⚔️ TACACS+ vs. RADIUS: Know the Differences
| Feature | TACACS+ | RADIUS |
|---|---|---|
| Protocol | TCP (port 49) | UDP (1812/1813) |
| Encryption | Full payload | Password only |
| AAA Separation | Yes – Auth, AuthZ, and Acct split | No – Auth & AuthZ combined |
| Vendor | Cisco | Open standard |
| Use Case | Device access (routers/switches) | Network access (Wi-Fi, VPN, 802.1X) |
🚦 Choosing the Right Tool
Use TACACS+ when:
- You're controlling who can configure network gear.
- You need granular command-level authorization.
- You're in a Cisco-dominant shop.
Use RADIUS when:
- You’re authenticating user access to the network.
- You're integrating with Active Directory or cloud identity providers.
- You're managing Wi-Fi, VPN, or 802.1X access control.
🔚 Final Thoughts
⚠️ Note: While TACACS+ may not be as dominant as it once was, it remains a trusted AAA protocol—especially in environments that demand strong security, fine-grained access control, and detailed auditing. That said, support is beginning to fade on some platforms, so organizations should evaluate alternative authentication options where appropriate.
AAA isn’t just a framework — it’s your first line of defense. Understanding the strengths of TACACS+ and RADIUS helps you apply the right protocol in the right place.
Security isn't just about blocking the bad. It's also about knowing who’s doing what — and when.
🚀 Next Step: Go Hands-On
Ready to put it into practice?
We’re taking the AAA concepts from this post and putting them to the test using the same topology from my “🚀 Phase 4 – Ring Around the Backbone: Simulating a Protected Transport Core — with my Raspberry Pi as the centralized TACACS+/RADIUS server and Cisco IOS and Juniper devices as clients.
➡️ Subscribe to my blog and be notified when Phase 5 drops – 🧠 Securing the Backbone: Integrating AAA with TACACS+ and RADIUS
If this post helped clarify the chaos, give it a share or leave a comment below (after subscribing 🔐). And check out my other stuff at brysteele.com.
Until next time — stay curious, stay secure. ☠️🔐
✌️OUT!
--Bryan

