🛡️ SSH Host Key Has Changed? Here’s How to Fix It
Ran into an SSH warning after reimaging your Pi or server? Don’t panic — here’s how to safely fix host key mismatch errors on macOS.

Whether you're managing Raspberry Pis, servers, cloud VMs, or remote boxes, you've likely seen this ominous message when trying to SSH in:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
...
Offending ECDSA key in /Users/<your-user>/.ssh/known_hosts:14
Host key verification failed.Don’t panic — it's not an attack (probably). This usually happens when you've:
- Re-flashed or re-imaged a device (like a Raspberry Pi)
- Rebuilt or reinstalled the OS on a server or VM
- Connected to a different host that reused an old IP
- The device at that IP address has changed SSH keys
Your computer is just being cautious to protect against spoofing. SSH is just warning you that the fingerprint of the remote machine changed, and it's trying to protect you from a possible man-in-the-middle attack.
🔧 What Does This Mean?
SSH stores fingerprints of remote hosts you've previously connected to in the file:
~/.ssh/known_hostsWhen the host key changes (e.g., due to OS reinstallation), SSH notices it doesn’t match what’s stored and halts the connection to prevent impersonation.
This applies to:
- Raspberry Pi
- Ubuntu/Debian/CentOS/Arch servers
- Cloud VMs (AWS, Azure, etc.)
- Docker containers with SSH enabled (rare)
A Few Ways to Fix This
✅ My Way:
This is my most common way, mainly because whenever I get this warning, I never remember the syntax for any of the other ways. So, I just delete the whole file and start from a clean slate:
rm /Users/<your-user>/.ssh/known_hostsThis will delete the whole file and all keys in it. You will just have to click yes again, when establishing any SSH sessions.✅ Option 2: Remove the offending key (line 14)
SSH usually tells you exactly which line is bad. Example:
Offending ECDSA key in /Users/<your-user>/.ssh/known_hosts:14You can surgically delete just the bad line:
sed -i '' '14d' ~/.ssh/known_hosts
Or open and edit it manually:
sudo nano ~/.ssh/known_hosts- Scroll to line 14
- Delete that line
- Save and exit (
Ctrl + X, thenY, thenEnter)
✅ Option 3: Remove the whole host entry by IP or Hostname
This method is cleaner and safer:
ssh-keygen -R 172.16.15.10Or by hostname:
ssh-keygen -R my-server.localSSH will delete the key entry for that host so it doesn’t complain the next time.
🔁 Now try again:
ssh steeletekk@172.16.15.10
Or:
ssh user@my-server.localYou’ll be prompted:
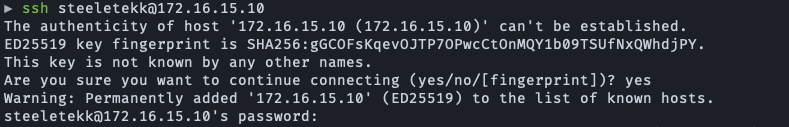
Typeyes, enter your password, and you’re in.
✅ We are now logged in to a headless Raspberry Pi running Raspberry Pi OS Lite
Why This Is a Good Thing
This is SSH doing its job: protecting you from man-in-the-middle attacks. It’s noisy, but necessary. When you’re regularly rebuilding VMs, Pi images, servers or home lab gear, it becomes part of your workflow.
✨ Tip for the Future
Give your devices static IPs or hostnames and document them. This avoids confusion when connecting across rebuilds.
Until next time — may your fingerprints match and your SSH tunnels stay encrypted ✌️Out!
-Bryan

